
Menteri 'de facto' undang-undang, yang sering dikaitkan dengan tesisnya itu, telah mengumumkan rencana serangan ‘peluru berpandu’ terhadap musuh khayalan di alam siber. Senjata yang hebat ini dikatakan menepati sasarannya, berbeza dengan model terdahulu yang mengecewakan. Bukan sahaja ia gagal menghancurkan sasarannya, tetapi ia mudah melantun balik untuk menjejaskan ‘buah kerandut’ pahlawan-pahlawan teknologi mereka yang ketandusan pengalaman. Kini, syak wasangka umum sudah pun diperakui. Perbuatan menggodam (hacking) laman-laman web yang begitu dedikasi mendedahkan salahlaku ahli-ahli politik Malaysia yang jijik itu disyaki telah dibiayai oleh menteri-menteri Malaysia sendiri. Namun, sehingga kini perkara itu masih belum disahkan. Pengumuman menteri tentang peperangan alam siber itu, bererti peperangan akan semakin menggila. Perkara ini akan menjadi lebih terperinci, sehinggakan terserlah nanti ketidak-seimbangan terhadap agihan sumber. Kita tentu ingat akan beberapa konflik di Asia Tenggara, di mana kuasa dan kecanggihan senjata pihak yang berkuasa beradu-domba melawan taktik gerila yang bersenjata ringan tetapi lebih lincah daripada pencabarnya. Babak pertempuran telah dipindah masuk untuk disesuaikan dengan suasana siber yang tidak bersempadan dan tidak mudah dipertahankan. Semua itu adalah khayalan, yang diberi sokongan persis satu permainan komputer, dengan penggunaan teknologi yang baru. Masalahnya dengan parti-yang-berkuasa ini adalah mereka kelihatan telah mengambil semua itu dengan serius sekali. Pertikaian kecil yang terjadi, yang tertumpu kepada kesungguhan untuk mengelakkan penapisan secara terus, kini berubah menjadi parah, dengan adanya niat kerajaan untuk bertindak kasar. Ini akan melibatkan jentera perundangan negara , bersama-sama dengan senjata terulungnya, polis cawangan khas (SB), yang bertindak secara fizikal untuk mencekup musuh dan komputer/ senjatanya, kedua-duanya akan melalui soal-siasat yang intensif. Hanya segelintir yang terlepas deraan ini. Ada yang akan menghilangkan untuk selamanya. Ramai yang akan muncul semula (dibebaskan) tanpa sebarang ingatan, satu fenomena yang sukar untuk dijelaskan mengikut pemahaman insani. Di dalam banyak kes, mereka yang ‘mati otaknya’ dan terpaksa bergantung penuh kepada orang lain ini, dibawa ke depan mahkamah hanya untuk memerhati perjalanan kes pendakwaan ke atas diri mereka. Hakim tidak mudah perasan betapa manusia yang berada di dalam kandang orang salah itu adalah zombi yang tidak boleh berfikir lagi dan tidak dapat memahami prosiding mahkamah. Polis cawangan khas memang pakar di dalam putar-balik minda (turning) mangsanya, dan ini membawa maksud menterbalikkan mereka menjadi orang yang terlalu lemah dan tidak berdaya untuk berbuat apa-apa. Memang tiada percubaan untuk melindungi dan mempertahankan insan yang lemah ini, sama ada oleh peguam yang dilantik atau hakim yang duduk mengadili kes. Ia adalah satu persendaan kepada keadilan, ala Malaysia. Dunia pasti akan dapat melihat banyak lagi kes yang serupa di masa yang akan datang. Tugasan menteri undang-undang semakin jelas digariskan. Porfolionya kini termasuk serangan baru yang bakal dilancarkan ke atas Internet., terutamanya laman-laman web yang berbisa. Beliau bercadang untuk mengnyahkan laman tertentu pilihannya sendiri, yang mungkin dianggap bersifat penghinaan oleh pemilik/ pengurus laman web. Ia membawa maksud penghapusan maklumat secara teknologi. Keadaan yang sama berlaku di dalam Third Reich (regim Nazi), satu lagi regim yang bersifat kuku besi. Menteri yang patuh itu tidak berkelayakan untuk memulakan perang siber. Pemahamannya tentang teknologi baru hanya terhad kepada mengupah penggodam-penggodam komputer (hackers) untuk menyebabkan kerosakan dan menggaji pekerja-pekerja kerajaan untuk mengirim virus-virus kepada pihak-pihak pembangkang melalui emel. MITI, yang berkaitan dengan hubungan perniagaan antarabangsa, baru-baru ini didapati bersalah kerana dengan sengaja menghantar virus-virus kepada alamat-alamat yang terpilih, walaupun ini kemudiannya dinafikan, di atas alasan ‘tidak sengaja’. Bukti-bukti yang ada menunjukkan sebaliknya. Menteri yang patuh ini mula menampakkan dirinya sebagai menteri maklumat songsang, lebih banyak terlibat di dalam menyalah-tafsirkan undang-undang dari melaksanakannya. Penelitian yang lebih rapi tentang bahasa yang digunakannya mengundang perbandingan dengan penggunaan komputer terhadap tesis yang telah dihasilkannya. Hasilnya memudahkan tekaan betapa wujudnya jejari lain yang memegang penanya, dulu. Keengganan beliau memperakui hasil kerja tersebut mempermudahkan andaian betapa memang wujud kelompongan dalam pertalian hubung-kait itu. Penyalahgunaan media cetak dan elektronik memang menjadi pilihan regim diktator pada satu masa dahulu. Penggunaan kaedah yang serupa bagi mengawal komunikasi dan berita akan gagal dalam zaman yang baru, satu perkara yang menteri-menteri di Malaysia nampaknya tidak berupaya untuk memahaminya. Bilangan laman web adalah melebihi sebarang keupayaan untuk memusnahkannya, dan ia boleh diklonkan, disalin secara ‘mirror image’ dan diwujudkan semula jauh lebih pantas lagi dari sebarang usaha untuk mengenal-pasti dan menyeranginya. Menteri berkenaan barangkali boleh merujuk kepada satu kes di mana satu perisian komputer dihasilkan bagi membolehkan pemindahan dari CD dilakukan. Apabila mahkamah mengarahkan laman web ini untuk membuang tawaran tersebut, perisian komputer itu dengan cepatnya disebarkan kepada lebih dari 1500 laman baru dalam beberapa jam sahaja. Begitulah hebatnya keupayaan internet untuk menghalang pengawalan terhadap isi kandungannya. Walaupun kenyataan-kenyataan umum dibuat bahawa pengisytiharan perang yang baru itu bukanlah merupakan langkah penapisan Internet, adalah sukar untuk mengenepikan kesimpulan ini. Jika tidak, bagaimana pula cara menilainya? Jika ini merupakan satu pengisytiharan perang, bahana akibat yang akan tercetus adalah dahsyat sekali. Kemampuan pemilik bebas komputer untuk bertindak-balas adalah menakutkan sekali. Ia mungkin bermula dengan pemboikotan firma-firma komputer yang menggunakan komponen elektronik bikinan Malaysia, sehinggalah kepada usaha mengnyahkan semua laman web kerajaan Malaysia. Keseluruhan struktur IT Malaysia memang terdedah pada bahaya Satu gencatan senjata yang segera seharusnya menjadi pilihan parti-yang-berkuasa. Seandainya serangan ke atas pelajar-pelajar berterusan, dan para tahanan ISA tidak dibebaskan, Bursa Saham Kuala Lumpur (BSKL) boleh diserang oleh jurutera-jurutera muda yang memuncak kebenciannya akibat dari taktik-taktik penindasan yang digunakan. Kemudahan IT yang lain juga terdedah kepada bentuk ancaman yang serupa. Parti-yang-berkuasa di Malaysia belum bersedia untuk menghadapi sebarang konfrontasi yang aktif di medan pertempuran siber. Diharapkan menteri yang dikatakan setia itu memahami masalah ini.
Monday, November 8, 2010
Perang Siber
Posted by lah at 6:07 PM 0 comments
Jenayah siber

jenayah Siber. Mengapa sukar dibendung
Kemunculan Internet sebagai alat komunikasi terkini menjanjikan satu wadah penyebaran maklumat yang memantapkan ilmu dan maklumat. Oleh kerana tiada siapa yang dapat mengawal perjalanan maklumat di dunia siber, berjuta-juta laman web telah dihidupkan. Bermacam-macam maklumat (sama ada benar atau salah), idea, ideologi, propaganda dan tidak kurang juga pornografi disebarkan melalui Internet.
Pada masa yang sama, kebebasan maklumat yang dijanjikan oleh dunia siber ini menimbulkan rasa gerun bagi pihak pentadbir sesetengah negara yang selama ini mahu mengongkong kebebasan bersuara, berfikir dan berpendapat penduduk mereka.
Posted by lah at 6:04 PM 0 comments
Sunday, November 7, 2010
Bus network topology
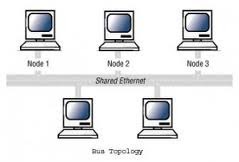

In local area networks where bus topology is used, each machine is connected to a single cable. Each computer or server is connected to the single bus cable through some kind of connector. A terminator is required at each end of the bus cable to prevent the signal from bouncing back and forth on the bus cable. A signal from the source travels in both directions to all machines connected on the bus cable until it finds the MAC address or IP address on the network that is the intended recipient. If the machine address does not match the intended address for the data, the machine ignores the data. Alternatively, if the data does match the machine address, the data is accepted. Since the bus topology consists of only one wire, it is rather inexpensive to implement when compared to other topologies. However, the low cost of implementing the technology is offset by the high cost of managing the network. Additionally, since only one cable is utilized, it can be the single point of failure. If the network cable breaks, the entire network will be down.
Posted by lah at 6:27 PM 0 comments
ring network
A ring network is a network topology in which each node connects to exactly two other nodes, forming a single continuous pathway for signals through each node - a ring. Data travels from node to node, with each node along the way handling every packet.
Because a ring topology provides only one pathway between any two nodes, ring networks may be disrupted by the failure of a single link[1]. A node failure or cable break might isolate every node attached to the ring. FDDI networks overcome this vulnerability by sending data on a clockwise and a counterclockwise ring: in the event of a break data is wrapped back onto the complementary ring before it reaches the end of the cable, maintaining a path to every node along the resulting "C-Ring". 802.5 networks -- also known as IBM Token Ring networks -- avoid the weakness of a ring topology altogether: they actually use a star topology at the physical layer and a Multistation Access Unit (MAU) to imitate a ring at the datalink layer.
Many ring networks add a "counter-rotating ring" to form a redundant topology. Such "dual ring" networks include Spatial Reuse Protocol, Fiber Distributed Data Interface (FDDI), and Resilient Packet Ring.
Posted by lah at 6:24 PM 0 comments
star topology
Star networks are one of the most common computer network topologies. In its simplest form, a star network consists of one central switch, hub or computer, which acts as a conduit to transmit messages.[1] Thus, the hub and leaf nodes, and the transmission lines between them, form a graph with the topology of a star. If the central node is passive, the originating node must be able to tolerate the reception of an echo of its own transmission, delayed by the two-way transmission time (i.e. to and from the central node) plus any delay generated in the central node. An active star network has an active central node that usually has the means to prevent echo-related problems.
The star topology reduces the chance of network failure by connecting all of the systems to a central node. When applied to a bus-based network, this central hub rebroadcasts all transmissions received from any peripheral node to all peripheral nodes on the network, sometimes including the originating node. All peripheral nodes may thus communicate with all others by transmitting to, and receiving from, the central node only. The failure of a transmission line linking any peripheral node to the central node will result in the isolation of that peripheral node from all others, but the rest of the systems will be unaffected. [2]
It is also designed with each node (file servers, workstations, and peripherals) connected directly to a central network hub, switch, or concentrator.
Data on a star network passes through the hub, switch, or concentrator before continuing to its destination. The hub, switch, or concentrator manages and controls all functions of the network. It is also acts as a repeater for the data flow. This configuration is common with twisted pair cable. However, it can also be used with coaxial cable or optical fibre cable.
Posted by lah at 6:13 PM 0 comments
Tuesday, November 2, 2010
Tuesday, June 29, 2010
Sunday, June 20, 2010
Network topology
Topology can be considered as a virtual shape or structure of a network. This shape actually does not correspond to the actual physical design of the devices on the computer network. The computers on the home network can be arranged in a circle shape but it does not necessarily mean that it presents a ring topology.
Any particular network topology is determined only by the graphical mapping of the configuration of physical and/or logical connections between nodes. The study of network topology uses graph theory. Distances between nodes, physical interconnections, transmission rates, and/or signal types may differ in two networks and yet their topologies may be identical.
A Local Area Network (LAN) is one example of a network that exhibits both a physical topology and a logical topology. Any given node in the LAN has one or more links to one or more nodes in the network and the mapping of these links and nodes in a graph results in a geometrical shape that may be used to describe the physical topology of the network. Likewise, the mapping of the data flow between the nodes in the network determines the logical topology of the network. The physical and logical topologies may or may not be identical in any particular network.
Posted by lah at 7:07 PM 0 comments
Computer architecture
It may also be defined as the science and art of selecting and interconnecting hardware components to create computers that meet functional, performance and cost goals.
Computer architecture comprises at least three main subcategories:[1]
Instruction set architecture, or ISA, is the abstract image of a computing system that is seen by a machine language (or assembly language) programmer, including the instruction set, word size, memory address modes, processor registers, and address and data formats.
Microarchitecture, also known as Computer organization is a lower level, more concrete and detailed, description of the system that involves how the constituent parts of the system are interconnected and how they interoperate in order to implement the ISA.[2] The size of a computer's cache for instance, is an organizational issue that generally has nothing to do with the ISA.
System Design which includes all of the other hardware components within a computing system such as:
System interconnects such as computer buses and switches
Memory controllers and hierarchies
CPU off-load mechanisms such as direct memory access (DMA)
Issues like multiprocessing.
Once both ISA and microarchitecture have been specified, the actual device needs to be designed into hardware. This design process is called implementation. Implementation is usually not considered architectural definition, but rather hardware design engineering.
Implementation can be further broken down into three (not fully distinct) pieces:
Logic Implementation — design of blocks defined in the microarchitecture at (primarily) the register-transfer and gate levels.
Circuit Implementation — transistor-level design of basic elements (gates, multiplexers, latches etc) as well as of some larger blocks (ALUs, caches etc) that may be implemented at this level, or even (partly) at the physical level, for performance reasons.
Physical Implementation — physical circuits are drawn out, the different circuit components are placed in a chip floorplan or on a board and the wires connecting them are routed.
Posted by lah at 7:00 PM 0 comments
Computer network
Posted by lah at 6:40 PM 0 comments
Wednesday, May 5, 2010
Function of OS
System tools (programs) used to monitor computer performance, debug problems, or maintain parts of the system.
A set of libraries or functions which programs may use to perform specific tasks especially relating to interfacing with computer system components.
The operating system makes these interfacing functions along with its other functions operate smoothly and these functions are mostly transparent to the user.
Posted by lah at 6:03 PM 0 comments
Operating system
Because early computers were often built for only a single task, operating systems did not exist in their proper form until the 1960s.[4] As computers evolved into being devices that could run different programs in succession, programmers began putting libraries of common programs (in the form of computer code) onto the computer in order to avoid duplication and speed up the process. Eventually, computers began being built to automatically switch from one task to the next. The creation of runtime libraries to manage processing and printing speed came next, which evolved into programs that could interpret different types of programming languages into machine code. When personal computers by companies such as Apple Inc., Atari, IBM and Amiga became popular in the 1980s, vendors began adding features such as software scheduling and hardware maintenance.
An operating system can be divided into many different parts. One of the most important parts is the kernel, which controls low-level processes that the average user usually cannot see: it controls how memory is read and written, the order in which processes are executed, how information is received and sent by devices like the monitor, keyboard and mouse, and deciding how to interpret information received by networks. The user interface is the part of the operating system that interacts with the computer user directly, allowing them to control and use programs. The user interface may be graphical with icons and a desktop, or textual, with a command line. Another similar feature is an Application programming interface, which is a set of services and code libraries that let applications interact with one another, as well as the operating system itself. Depending on the operating system, many of these components may not be considered an actual part. For example, Windows considers its user interface to be part of the operating system, while many versions of Linux do not.
Posted by lah at 5:59 PM 0 comments
Secondary storage
In modern computers, hard disk drives are usually used as secondary storage. The time taken to access a given byte of information stored on a hard disk is typically a few thousandths of a second, or milliseconds. By contrast, the time taken to access a given byte of information stored in random access memory is measured in billionths of a second, or nanoseconds. This illustrates the very significant access-time difference which distinguishes solid-state memory from rotating magnetic storage devices: hard disks are typically about a million times slower than memory. Rotating optical storage devices, such as CD and DVD drives, have even longer access times. With disk drives, once the disk read/write head reaches the proper placement and the data of interest rotates under it, subsequent data on the track are very fast to access. As a result, in order to hide the initial seek time and rotational latency, data are transferred to and from disks in large contiguous blocks.
When data reside on disk, block access to hide latency offers a ray of hope in designing efficient external memory algorithms. Sequential or block access on disks is orders of magnitude faster than random access, and many sophisticated paradigms have been developed to design efficient algorithms based upon sequential and block access . Another way to reduce the I/O bottleneck is to use multiple disks in parallel in order to increase the bandwidth between primary and secondary memory.[2]
Some other examples of secondary storage technologies are: flash memory (e.g. USB flash drives or keys), floppy disks, magnetic tape, paper tape, punched cards, standalone RAM disks, and Iomega Zip drives.
The secondary storage is often formatted according to a file system format, which provides the abstraction necessary to organize data into files and directories, providing also additional information (called metadata) describing the owner of a certain file, the access time, the access permissions, and other information.
Most computer operating systems use the concept of virtual memory, allowing utilization of more primary storage capacity than is physically available in the system. As the primary memory fills up, the system moves the least-used chunks (pages) to secondary storage devices (to a swap file or page file), retrieving them later when they are needed. As more of these retrievals from slower secondary storage are necessary, the more the overall system performance is degraded.
Posted by lah at 5:57 PM 0 comments
Primary storage
Historically, early computers used delay lines, Williams tubes, or rotating magnetic drums as primary storage. By 1954, those unreliable methods were mostly replaced by magnetic core memory, which was still rather cumbersome. Undoubtedly, a revolution was started with the invention of a transistor, that soon enabled then-unbelievable miniaturization of electronic memory via solid-state silicon chip technology.
This led to a modern random-access memory (RAM). It is small-sized, light, but quite expensive at the same time. (The particular types of RAM used for primary storage are also volatile, i.e. they lose the information when not powered).
As shown in the diagram, traditionally there are two more sub-layers of the primary storage, besides main large-capacity RAM:
Processor registers are located inside the processor. Each register typically holds a word of data (often 32 or 64 bits). CPU instructions instruct the arithmetic and logic unit to perform various calculations or other operations on this data (or with the help of it). Registers are technically among the fastest of all forms of computer data storage.
Processor cache is an intermediate stage between ultra-fast registers and much slower main memory. It's introduced solely to increase performance of the computer. Most actively used information in the main memory is just duplicated in the cache memory, which is faster, but of much lesser capacity. On the other hand it is much slower, but much larger than processor registers. Multi-level hierarchical cache setup is also commonly used—primary cache being smallest, fastest and located inside the processor; secondary cache being somewhat larger and slower.
Main memory is directly or indirectly connected to the central processing unit via a memory bus. It is actually two buses (not on the diagram): an address bus and a data bus. The CPU firstly sends a number through an address bus, a number called memory address, that indicates the desired location of data. Then it reads or writes the data itself using the data bus. Additionally, a memory management unit (MMU) is a small device between CPU and RAM recalculating the actual memory address, for example to provide an abstraction of virtual memory or other tasks.
As the RAM types used for primary storage are volatile (cleared at start up), a computer containing only such storage would not have a source to read instructions from, in order to start the computer. Hence, non-volatile primary storage containing a small startup program (BIOS) is used to bootstrap the computer, that is, to read a larger program from non-volatile secondary storage to RAM and start to execute it. A non-volatile technology used for this purpose is called ROM, for read-only memory (the terminology may be somewhat confusing as most ROM types are also capable of random access).
Many types of "ROM" are not literally read only, as updates are possible; however it is slow and memory must be erased in large portions before it can be re-written. Some embedded systems run programs directly from ROM (or similar), because such programs are rarely changed. Standard computers do not store non-rudimentary programs in ROM, rather use large capacities of secondary storage, which is non-volatile as well, and not as costly.
Posted by lah at 5:54 PM 0 comments
Storage
Posted by lah at 5:53 PM 0 comments
Tuesday, April 20, 2010
IP address
An Internet Protocol (IP) address is a numerical label that is assigned to devices participating in a computer network, that uses the Internet Protocol for communication between its nodes.[1] An IP address serves two principal functions: host or network interface identification and location addressing. Its role has been characterized as follows: "A name indicates what we seek. An address indicates where it is. A route indicates how to get there."[2]
The designers of TCP/IP defined an IP address as a 32-bit number[1] and this system, known as Internet Protocol Version 4 or IPv4, is still in use today. However, due to the enormous growth of the Internet and the resulting depletion of available addresses, a new addressing system (IPv6), using 128 bits for the address, was developed in 1995[3] and last standardized by RFC 2460 in 1998.[4] Although IP addresses are stored as binary numbers, they are usually displayed in human-readable notations, such as 208.77.188.166 (for IPv4), and 2001:db8:0:1234:0:567:1:1 (for IPv6).
The Internet Protocol also routes data packets between networks; IP addresses specify the locations of the source and destination nodes in the topology of the routing system. For this purpose, some of the bits in an IP address are used to designate a subnetwork. The number of these bits is indicated in CIDR notation, appended to the IP address; e.g., 208.77.188.166/24.
As the development of private networks raised the threat of IPv4 address exhaustion, RFC 1918 set aside a group of private address spaces that may be used by anyone on private networks. They are often used with network address translators to connect to the global public Internet.
The Internet Assigned Numbers Authority (IANA), which manages the IP address space allocations globally, cooperates with five Regional Internet Registries (RIRs) to allocate IP address blocks to Local Internet Registries (Internet service providers) and other entities
Posted by lah at 8:59 PM 0 comments
colour code
Authors of web pages have a variety of options available for specifying colors for elements of web documents. Colors may be specified as an RGB triplet in hexadecimal format (a hex triplet); they may also be specified according to their common English names in some cases. Often a color tool or other graphics software is used to generate color values.
The first versions of Mosaic and Netscape Navigator used the X11 color names as the basis for their color lists, as both started as X Window System applications.[3]
Web colors have an unambiguous colorimetric definition, sRGB, which relates the chromaticities of a particular phosphor set, a given transfer curve, adaptive whitepoint, and viewing conditions.[4] These have been chosen to be similar to many real-world monitors and viewing conditions, so that even without color management rendering is fairly close to the specified values. However, user agents vary in the fidelity with which they represent the specified colors. More advanced user agents use color management to provide better color fidelity; this is particularly important for Web-to-print applications.
Posted by lah at 8:54 PM 0 comments
Crossover cable

The crossing wires in a cable or in a connector adaptor allows:
connecting two devices directly, output of one to input of the other,
letting two terminal (DTE) devices communicate without an interconnecting hub knot, i.e. PCs,
linking two or more hubs, switches or routers (DCE) together, possibly to work as one wider device.
[edit] Examples
a Null modem of RS-232
Ethernet crossover cable
Rollover cable
A loopback is a type of degraded "one side crosslinked connection" connecting a port to itself, usually for test purposes.
Use crossover cables for the following connections: Switch to switch, Switch to hub, Hub to hub, Router to router, PC to PC, Router to PC
[edit] Other technologies
Some connection standards use different balanced pairs to transmit data, so crossover cables for them have different configurations to swap the transmit and receive pairs:
Twisted pair Token ring uses T568B pairs 1 and 3 (the same as T568A pairs 1 and 2), so a crossover cable to connect two Token Ring interfaces must swap these pairs, connecting pins 4, 5, 3, and 6 to 3, 6, 4, and 5 respectively.
A T1 cable uses T568B pairs 1 and 2, so to connect two T1 CSU/DSU devices back-to-back requires a crossover cable that swaps these pairs. Specifically, pins 1, 2, 4, and 5 are connected to 4, 5, 1, and 2 respectively.
A 56K DDS cable uses T568B pairs 02 and 04, so a crossover cable for these devices swaps those pairs (pins 01, 02, 07, and 08 are connected to 07, 08, 01, and 02 respectively).
Posted by lah at 8:47 PM 0 comments
straight cable (cat5)


 Both the T-568A and the T-568B standard Straight-Through cables are used most often as patch cords for your Ethernet connections. If you require a cable to connect two Ethernet devices directly together without a hub or when you connect two hubs together, you will need to use a Crossover cable instead.
Both the T-568A and the T-568B standard Straight-Through cables are used most often as patch cords for your Ethernet connections. If you require a cable to connect two Ethernet devices directly together without a hub or when you connect two hubs together, you will need to use a Crossover cable instead.Ethernet Cable Instructions:
Pull the cable off the reel to the desired length and cut. If you are pulling cables through holes, its easier to attach the RJ-45 plugs after the cable is pulled. The total length of wire segments between a PC and a hub or between two PC's cannot exceed 100 Meters (328 feet) for 100BASE-TX and 300 Meters for 10BASE-T.
Start on one end and strip the cable jacket off (about 1") using a stripper or a knife. Be extra careful not to nick the wires, otherwise you will need to start over.
Spread, untwist the pairs, and arrange the wires in the order of the desired cable end. Flatten the end between your thumb and forefinger. Trim the ends of the wires so they are even with one another, leaving only 1/2" in wire length. If it is longer than 1/2" it will be out-of-spec and susceptible to crosstalk. Flatten and insure there are no spaces between wires.
Hold the RJ-45 plug with the clip facing down or away from you. Push the wires firmly into the plug. Inspect each wire is flat even at the front of the plug. Check the order of the wires. Double check again. Check that the jacket is fitted right against the stop of the plug. Carefully hold the wire and firmly crimp the RJ-45 with the crimper.
Check the color orientation, check that the crimped connection is not about to come apart, and check to see if the wires are flat against the front of the plug. If even one of these are incorrect, you will have to start over. Test the Ethernet cable.
Ethernet Cable Tips:
A straight-thru cable has identical ends.
A crossover cable has different ends.
A straight-thru is used as a patch cord in Ethernet connections.
A crossover is used to connect two Ethernet devices without a hub or for connecting two hubs.
A crossover has one end with the Orange set of wires switched with the Green set.
Odd numbered pins are always striped, even numbered pins are always solid colored.
Looking at the RJ-45 with the clip facing away from you, Brown is always on the right, and pin 1 is on the left.
No more than 1/2" of the Ethernet cable should be untwisted otherwise it will be susceptible to crosstalk.
Do not deform, do not bend, do not stretch, do not staple, do not run parallel with power cables, and do not run Ethernet cables near noise inducing components

Posted by lah at 8:34 PM 0 comments

Posted by lah at 8:04 PM 0 comments
Monday, March 22, 2010
Kaedah pemulihan virus

Kaedah pemulihan virus sahaja sebuah komputer terjejas oleh virus, komputer itu biasanya tidak selamat untuk diteruskan penggunaannya, tanpa memasang semula sistem pengendalian komputer itu. Bagaimanapun, terdapat sebilangan cara pemulihan yang sedia ada selepas sesuatu komputer terjejas oleh virus. Tindakan-tindakan yang boleh diambil bergantung kepada teruknya jenis virus yang terlibat.
Posted by lah at 7:22 PM 1 comments
Penghapusan virus
.jpg)
Satu langkah yang mungkin untuk menghapuskan virus yang wujud dalam Windows XP ialah penggunaan alat yang dikenali sebagai Pemulihan Sistem (System Restore). Alat ini memulihkan registri dan fail-fail sistem yang genting kepada titik semak yang dahulu.
Seringnya, sesebuah virus akan mengakibatkan sistem komputer tergantung, dengan pembutan semula keras akan merosakkan titik pemulihan sistem daripada hari yang sama. Titik pemulihan daripada hari-hari sebelumnya harus masih berkesan, asalkan virus itu tidak direka untuk merosakkan fail-fail pemulihan. Bagaimanapun, sesetengah virus, misalnya virus CiaDoor, akan mematikan pemulihan sistem serta alat-alat lain yang penting seperti Pengurus Tugas (Task Manager) dan penggesa. Virus mengubah suai registri dengan cara yang tepat sama dengan para pentadbir mematikan alat-alat tersebut atas berbagai-bagai alasan daripada pengguna-pengguna terhad, kecuali bahawa virus menyekat semua pengguna, termasuk juga pentadbir. Apabila sesuatu alat terjangkit diaktifkan, virus itu akan memaparkan pesanan, "Pengurus Tugas telah dimatikan oleh pentadbir anda", walaupun jika pengguna yang mencuba memulakan atur cara adalah pentadbir pada dirinya.
Posted by lah at 7:20 PM 0 comments
virus
.jpg)
Virus komputer adalah nama yang diambil dari virus biologi, merupakan program komputer yang berupaya menyalin dirinya sendiri dan menjangkiti komputer tanpa kebenaran ataupun pengetahuan pengguna. Bagaimanapun perkataan virus biasanya digunakan bagi merujuk kepada pelbagai jenis perisian perosak yang berlainan. Virus yang asal mungkin mengubah suai salinannya atau salinan itu sendiri yang mengubah suai dirinya, seperti dalam virus metamorf. Virus hanya boleh tersebar apabila hosnya sampai ke komputer lain, contohnya melalui rangkaian atau perantara mudah alih seperti cakera liut, cakera padat atau pemacu kilat USB. Selain itu, virus juga boleh merebak dengan menjangkiti fail pada sistem fail rangkaian atau mana-mana sistem fail yang dicapai komputer lain.
Sesetengah virus direka untuk menjejaskan komputer dengan merosakkan atur cara, menghapuskan fail, atau memformat semula cakera keras, manakala virus-virus yang lain direka bukan untuk merosakkan apa-apa, tetapi hanya untuk menyalin diri dan mungkin untuk menonjolkan kewujudannya melalui pemaparan teks, video, atau pesanan audio. Walaupun virus yang kedua ini tidak berbahaya, ia juga boleh menimbulkan masalah kepada pengguna komputer kerana ia menelan ingatan komputer yang digunakan oleh atur cara yang sah. Oleh yang demikian, ia seringnya mengakibatkan tindakan yang tidak menentu dan boleh mengakibatkan kerosakan sistem. Selain itu, banyak virus juga mengandungi pepijat yang boleh mengakibatkan kerosakan sistem dan kehilangan data.
Virus komputer kekadangnya dikelirukan dengan cecacing komputer dan kuda Trojan. Kedua-dua ini berbeza dari segi bahawa cecacing boleh merebak ke komputer yang lain tanpa memerlukannya dipindahkan sebagai sebahagian fail perumah, manakala kuda Trojan adalah fail yang kelihatan tidak berbahaya sehingga dilaksanakan. Berbeza dengan virus, kuda Trojan juga tidak memasukkan kodnya ke dalam fail-fail komputer yang lain.
Banyak komputer peribadi kini dihubungkan dengan internet serta rangkaian kawasan setempat dan dengan itu, memudahkan perebakan virus. Ia mengambil kesempatan yang diberikan oleh perkhidmatan rangkaian seperti sistem-sistem Jaringan Sejagat, e-mel, dan pengongsian fail untuk merebak dan dengan itu, mengaburi perbezaan antara virus dengan cecacing komputer. Tambahan pula, sesetengah sumber menggunakan istilah alternatif yang mentakrifkan virus sebagai mana-mana bentuk perisian jahat penyalinan diri.
Posted by lah at 7:08 PM 0 comments
Monday, March 8, 2010
Multimedia
google_protectAndRun("ads_core.google_render_ad", google_handleError, google_render_ad);
Posted by lah at 6:51 PM 0 comments























 Kuala Lumpur Time
Kuala Lumpur Time